
- What We Do
-
Network Monitoring
Network Monitoring
Discover the Full 360° View of Your IT Network and Infrastructure!
Leverage our AI-driven monitoring and management solutions to attain complete oversight and governance of your IT and network infrastructure. In today's data-centric environment, businesses thrive on information. We diligently capture and analyse all events occurring within your diverse and hybrid IT setup, generating invaluable insights to steer your business towards success.

-
Unified Infrastructure Monitoring System
Unified Infrastructure Monitoring System
Empower Your Business with Unified Infrastructure Monitoring
Experience full-stack monitoring of your infrastructure through a single, integrated platform. Our comprehensive solution offers monitoring, log indexing, visualization, and alerting capabilities across your hybrid infrastructure. By providing IT operations leaders with data-driven intelligence, we enable them to deliver better business outcomes and ensure the seamless operation of your organization

-
Network Configuration Management (NCM)
Network Configuration Management (NCM)
Effortless Network Transformation: Smart Network Configuration Solutions
Discover effortless network management with our smart configuration solutions. Save time and enhance performance with advanced automation and remediation runbooks from 247 Tech

-
Log Analysis & Network Flow
Log Analysis & Network Flow
Empower Your Organization with Comprehensive Log Analysis and Network Flow Solutions
Achieve comprehensive insight on a large scale with our advanced log analysis and network flow solutions. Gain high-level analytics to swiftly investigate and troubleshoot issues. Our tools streamline the collection, analysis, monitoring, and visualization of data for your organization, providing unparalleled clarity and efficiency.

-
Unified Infrastructure Monitoring System
-
Cybersecurity & Protection
Cybersecurity & Protection
Unmatched Security for Your Enterprise.
Our comprehensive solutions safeguard your entire ecosystem – people, processes, and technologies – from breaches, ransomware, and cyberattacks. Leveraging cutting-edge technology and our industry-leading expertise, we deliver the ultimate defense for your modern enterprise.

-
Cybersecurity (Firewall, Endpoint & Server)
Cybersecurity (Firewall, Endpoint & Server)
Unwavering Cybersecurity Defense.
In today's complex IT landscape, cybersecurity is no longer optional. Our comprehensive solutions provide complete protection for your network, endpoints, and servers. Leveraging cutting-edge AI technology and our team of security specialists, we proactively prevent and expertly handle malicious activities like ransomware, phishing, malware, and more.

-
Zero Trust Network Access (ZTNA)
Zero Trust Network Access (ZTNA)
Zero Trust Access for Unparalleled Control.
In today's access-driven world, application security is critical. Our ZTNA solution implements a "zero trust" approach, verifying every user and device attempting to access your applications. Multi-factor authentication adds an extra layer of security, ensuring only authorized individuals with compliant devices gain access.

-
Network Access Control (NAC)
Network Access Control (NAC)
Command Your Network- Complete Visibility and Control.
See everything, control everything, and automate your response – that's the power of Network Access Control (NAC). Our NAC solution grants you complete visibility and control over every device connecting to your network.

-
Email Security & Mail Gateway
Email Security & Mail Gateway
Secure Your Inbox with Powerful Email Security.
Drowning in spam and worried about phishing attacks? You're not alone. Malicious emails are a major threat to IT security. Our expertly engineered Email Security Gateway stands guard, filtering out spam, phishing attempts, malware, and other fraudulent content before they reach your inbox.

-
Secure SD-WAN and SASE
Secure SD-WAN and SASE
Unleash Network Agility & Security.
Empower your users and locations with seamless connectivity. Our combined Secure SD-WAN and SASE solution gives you centralized control over your entire network, spanning remote users, edge devices, branch offices, IoT devices, and beyond.

-
Identity & Access Management
Identity & Access Management
Lock Down Access. Secure Your Digital Identity
In today's digital world, who has access to what matters most? Identity & Access Management (IAM) is your key to complete control. Our IAM solution lets you create, monitor, and manage every digital identity within your organization.

-
SIEM & SOAR
SIEM & SOAR
Smarter Security Operations.
Security threats are relentless, bombarding you with daily alerts. But what if you could sift through the noise and focus on what truly matters? SIEM & SOAR is the answer.
-
Business Continuity & Encryption
Business Continuity & Encryption
Create an impenetrable shield.
Disruptions happen. From natural disasters to cyberattacks, unexpected events can cripple your business. That's where Business Continuity planning comes in. We help you develop a resilient & contingent business plan to ensure critical functions keep running, no matter what life throws your way.

-
Vulnerability Assessment and Penetration Testing (VAPT)
Vulnerability Assessment and Penetration Testing (VAPT)
Don't Drown in Vulnerabilities.
Get a comprehensive view of your vulnerabilities across your entire IT infrastructure, including cloud platforms, IoT devices, and operational technology. Our dynamic and continuous assessments ensure you stay ahead of emerging threats.

-
Governance, Risk and Compliance
Governance, Risk and Compliance
Simplify Security. Strengthen Your Business.
Our Governance, Risk, and Compliance (GRC) solution takes the mystery out of cybersecurity. Monitor adherence to industry best practices, identify and manage potential threats, and ensure compliance with all relevant ISO standards.

-
Managed SOC
Managed SOC
Outpace Threats. Regain Control of Your Security.
In today's rapidly evolving digital world, your attack surface grows with every step towards innovation. This surge translates to a mountain of security alerts, burying your analysts in a never-ending triage, investigation, and remediation cycle. Our Managed SOC solution provides a highly-skilled team of security experts who seamlessly integrate with your existing infrastructure.

-
Cybersecurity (Firewall, Endpoint & Server)
-
IT Service Desk
IT Service Desk
Streamline Service Delivery.
Drowning in a sea of IT requests? Our ITSM service is your lifeline to simplified IT service management. Boost your team's productivity with lightning-fast ticketing, efficient issue resolution, and a completely revamped internal service experience.

-
Service Desk
Service Desk
Streamline Service Delivery.
Drowning in a sea of IT requests? Our ITSM service is your lifeline to simplified IT service management. Boost your team's productivity with lightning-fast ticketing, efficient issue resolution, and a completely revamped internal service experience.

-
Asset Management
Asset Management
Effortless IT & Non-IT Asset Management.
Say goodbye to asset spreadsheets and hello to complete control. Our IT asset management solution automates the entire lifecycle – from initial procurement to final disposal – for both IT and non-IT assets, across all your locations. Gain a unified view, streamline processes, and never lose track of an asset again.

-
Patch Management
Patch Management
Automated Vulnerability Detection & Patch Management.
Don't let outdated software leave your systems exposed. Our patch management software identifies vulnerabilities on workstations and servers, analyzes risks, and automates the patching process – all from a central hub. Simplify endpoint management, save IT time, and keep your network secure.
-
Service Desk
-
Telecom / ISP Billing & Bandwidth Management
Telecom / ISP Billing & Bandwidth Management
Your Partner for Tailored Business Solutions - Comprehensive Management Solutions:
Welcome to Comprehensive Management Solutions, your one-stop destination for customized solutions catering to a diverse range of businesses, including ISPs and Hotels. Our mission is to empower businesses like yours with innovative strategies to boost revenue and enhance customer satisfaction

-
Internet Billing & AAA
Internet Billing & AAA
Unlocking Versatility: A Single Solution with Multiple Features
Introducing our single solution with multiple features, designed to meet the diverse needs of businesses with ease and efficiency. Our highly flexible solution supports a wide range of protocols, ensuring seamless integration with various systems and devices. With robust authentication, authorization, and accounting capabilities, based on internet usage, you can trust our solution to safeguard your network and data. Take control of your bandwidth with our intuitive bandwidth control features, optimizing performance and enhancing the user experience. Plus, simplify your billing processes with our comprehensive billing management system, offering both prepaid and postpaid billing cycles for multiple services. Experience the power of versatility with our all-in-one solution today.

-
Cloud Service Provider (Private cloud & Colocation billing)
Cloud Service Provider (Private cloud & Colocation billing)
Unlocking Cloud Potential: Visibility and Control at Your Fingertips
At 247.Tech, we empower businesses with the tools they need to harness the full potential of cloud migration. With billions of dollars invested in cloud migration for storage, infrastructure, services, products, and operating systems, our platform ensures seamless access to systems and data from anywhere, at any time. Our intelligent monitoring platform provides unparalleled security for your data and resources, giving you complete control over your infrastructure. Whether you're managing storage, applications, or virtual machines, our platform offers visibility and control to optimize performance and maximize efficiency. This intelligent monitoring platform secures data and resources and gives you total control over infrastructure.

-
Bandwidth Management, Acceleration & Caching (CDN)
Bandwidth Management, Acceleration & Caching (CDN)
Boost Your Efficiency with Bandwidth Management, Acceleration & Caching (CDN)
In today's fast-paced digital landscape, bandwidth consumption is on the rise across all market segments. However, with this increase comes the challenge of controlling and preventing overconsumption, which can hinder productivity and efficiency. At our platform, we understand the importance of optimizing bandwidth usage to ensure smooth operations and enhance productivity. That's why we offer a centralized Bandwidth Controller solution designed to provide better visibility and control over your network resources. With our Bandwidth Management, Acceleration & Caching (CDN) services, you can streamline your operations, minimize bottlenecks, and accelerate your productivity to new heights. Experience the power of efficient bandwidth management with us today.
-
Captive Portal & High-Speed Internet Access (HSIA)
Captive Portal & High-Speed Internet Access (HSIA)
Transform Your Connectivity with Captive Portal & HSIA
Enhance your property's internet services with our Captive Portal and High-Speed Internet Access (HSIA) solutions. Deliver a seamless, secure, and branded online experience to your visitors while restricting unauthorized access. Our easy-to-install solution not only provides high-speed internet but also offers valuable marketing opportunities, turning your network into a powerful tool for user engagement and business growth.

-
Mobile Money & Digital Wallet
Mobile Money & Digital Wallet
Revolutionize Your Finances: Embracing the Era of Digital Currency
In today's fast-paced world, the digital revolution has transformed nearly every aspect of our lives, including how we manage our finances. Embracing digital currency opens up a world of possibilities, offering unparalleled convenience, security, and accessibility. With just a few taps on your smartphone or clicks on your computer, you can seamlessly send and receive money, pay bills, and make purchases online or in-store. Say goodbye to the limitations of cash and hello to the future of finance with digital currency.

-
Traffic Monitoring & Fraud Management
Traffic Monitoring & Fraud Management
Enhanced Security with Traffic Monitoring & Fraud Management
Our advanced Traffic Monitoring and Fraud Management solution comes with built-in security features to protect your network. With our Web filtering capability, network administrators can block user access to 37 categories of websites, including both HTTP and HTTPS traffic. This ensures a secure browsing environment and prevents access to potentially harmful or inappropriate content. The denial message displayed to users can be customized and branded according to your business needs, maintaining a consistent and professional image. Additionally, we offer multiple administration levels based on organizational roles, providing tailored access and control to enhance overall security for your business.

-
Network & 5G Monetization
Network & 5G Monetization
Maximizing Returns: Unleashing the Power of Network and 5G Monetization
Embark on a journey beyond mere connectivity and harness the full potential of your 5G investments with our innovative network and 5G monetization solutions. Our cutting-edge technology offers real-time policy design and implementation, bringing ultra-low latency and lightning-fast network speeds to enhance customer satisfaction. At our core, we're committed to helping you navigate the concept-to-cash lifecycle seamlessly. From ideation to execution, we collaborate closely with partners to swiftly build and launch irresistible offers that keep customers coming back for more. With our expertise and dedication, unlock new avenues for revenue generation and customer delight in the dynamic world of network and 5G monetization.

-
GPON
GPON
Experience Effortless Connectivity with G-PON
G-PON (Gigabit Passive Optical Network) redefines the landscape of data transmission with its unparalleled efficiency and versatility. Designed to meet the demands of modern connectivity, G-PON offers a streamlined solution for delivering Ethernet, TDM (Time Division Multiplexing), and ATM (Asynchronous Transfer Mode) traffic through optical cables. With G-PON, users can enjoy blazing-fast internet speeds while significantly reducing energy consumption, making it an ideal choice for environmentally conscious businesses and individuals. Say goodbye to sluggish connections and hello to effortless connectivity with G-PON.

-
Internet Billing & AAA
-
Networks, Wi-Fi, Computing & Storage
Networks, Wi-Fi, Computing & Storage
Unleash the Power of Scalable Network Technology
Do you manage a data centre, cloud environment, or campus network? Struggling to keep pace with growing demands and a complex IT landscape? We offer a revolutionary software-driven solution designed for today's dynamic needs.

-
Routing, Switching & Wi-Fi
Routing, Switching & Wi-Fi
Smart & Secure Network Solutions
Experience flawless connections and lightning-fast application performance. We go beyond just getting you online – we equip your network administrators with real-time insights to tackle problems instantly and keep your network running smoothly, even as your needs evolve.

-
Servers & Virtualization
Servers & Virtualization
Unlocking Agility and Efficiency: Servers & Virtualization Solutions
In today's dynamic business landscape, a powerful and adaptable IT infrastructure is essential. Our server and virtualization services empower you to achieve just that.

-
Storage (NAS, SAN, Cloud)
Storage (NAS, SAN, Cloud)
Unleash the Power of Flexible Data Storage
Our robust solutions, encompassing NAS, SAN, and cloud options, offer unparalleled flexibility and centralized control. Multiple users can access and collaborate on data 24/7, both on-premises and remotely. Standardized formatting and processing protocols ensure consistency and efficiency.

-
Hyperconvergence
Hyperconvergence
Simplify Your Data Centre: Embrace Hyperconvergence
Unleash agility and efficiency with hyperconverged infrastructure (HCI). This revolutionary approach combines compute, storage, and networking into a single, software-defined system.
-
Software Defined & Cloud Networking
Software Defined & Cloud Networking
Unleash the Power of Unified Cloud and Software-Defined Networking
Transform your network with a revolutionary approach that integrates the agility of software-defined networking (SDN) with the scalability of cloud networking. Our solution offers a highly secure, open, and programmable foundation
-
Data Back-Up
Data Back-Up
Safeguard Your Digital Assets: Efficient & Secure Data Backup and Recovery
Data loss can strike unexpectedly – a hardware malfunction, a sneaky virus, or even accidental deletion. Don't let these unforeseen events cripple your business. We offer a robust data backup and recovery solution designed to keep your critical information safe and accessible at all times.

-
Routing, Switching & Wi-Fi
-
Data Center, Power & Cooling
Data Center, Power & Cooling
Experience the future of data with eco-friendly efficiency.
We empower you to harness the power of cutting-edge servers fuelled by renewable energy sources. Our comprehensive solutions minimize your environmental impact while maximizing uptime and performance.
-
Data center & Cabling
Data center & Cabling
Harness the power of innovation without compromising our planet.
We're pioneering a new era of data centre solutions built on a foundation of sustainability. We offer cutting-edge servers powered by renewable energy resources, minimizing your environmental impact while maximizing uptime and performance.

-
Racks, Cabinets, Containments
Racks, Cabinets, Containments
Flexible & Expandable Data Centre Solutions
We offer innovative, on-demand modular solutions for racks, cabinets, and containment. These solutions are designed with flexibility and expandability in mind, allowing you to scale your data centre seamlessly as your needs evolve.
-
Copper & Fiber Systems – Cabling, Patch Panels
Copper & Fiber Systems – Cabling, Patch Panels
Unbreakable Connections for Peak Performance
Our comprehensive cabling and patch panel solutions are meticulously engineered to handle the ever-growing demands of high data volumes. Reduce latency, enhance throughput, and strengthen your Service Level Agreements (SLAs) with end-to-end connectivity you can trust.

-
GPON
GPON
Unleash Blazing Speeds, Eco-Friendly Power
Craving a cost-effective, sustainable solution for your data needs? GPON is your answer. This revolutionary technology utilizes optical cables to deliver lightning-fast internet, Ethernet, TDM, and ATM traffic – all while minimizing your environmental impact.

-
Backup Power (UPS) & Intelligent PDU
Backup Power (UPS) & Intelligent PDU
Uninterrupted Power
We empower you to achieve unwavering power stability with our comprehensive Backup Power (UPS) & Intelligent PDU solutions. This dynamic duo safeguards your data centre from the unexpected, ensuring uninterrupted uptime and optimal performance.
-
Cooling – Inrow, Rack Mounted
Cooling – Inrow, Rack Mounted
Safeguard Your Data
Data centres are the beating hearts of our digital world, but keeping them cool and secure can be a complex challenge. We offer a comprehensive suite of solutions to ensure your data centre operates in a safe and optimal environment. Our combined expertise in Cooling (In-Row & Rack-Mounted) and Fire Protection empowers you to achieve unwavering peace of mind.
-
HVAC & BMS
HVAC & BMS
Command Central for Your Building
A Building Management System (BMS) acts as the maestro of your building's operations, centralizing control and monitoring of various services. HVAC (Heating, Ventilation, and Air Conditioning) systems are a crucial component within this symphony.

-
Data center & Cabling
-
Unified Communication & Collaboration
Unified Communication & Collaboration
Create Powerful Business Connections
In today's hybrid business world, more meetings are held remotely than on premises. We offer solutions that elevate your communications to the next level. Our range of communication products provides excellent audio solutions, enabling you to have clear and impactful conversations. Enhance your business connections with our unified communication and collaboration tools.

-
Omni Channel Contact center and Helpdesk
Omni Channel Contact center and Helpdesk
Enhance Your Call Center Productivity With Next-Generation Communication Systems
We offer a comprehensive Contact Center solution that integrates outbound, inbound, and blended voice processes. Our system also includes Interactive Voice Response (IVR), recording, quality management, comprehensive reporting, and administrative capabilities. Increase sales, save money, and improve customer satisfaction with one all-encompassing solution!

-
Interactive Voice Response System (IVRS)
Interactive Voice Response System (IVRS)
Deliver Exceptional Service with Automated Call Handling
Our Interactive Voice Response System (IVRS) is designed to enhance customer service by efficiently managing incoming calls. With touch-tone detection capabilities, our IVR system automatically responds to callers with pre-recorded audio prompts, enabling seamless call handling and automatic information dissemination. Additionally, our IVRS features advanced functionalities such as Two Stage Calling, Advertisements, and Music-On-Hold, ensuring a professional and engaging caller experience.

-
Unified communications & Collaboration
Unified communications & Collaboration
Integrated Collaboration That Brings People Together In One Experience
Our Unified Communications (UC) solutions integrate various communication tools such as IP telephony, web and video conferencing, voice mail, mobility, desktop sharing, instant messaging, and presence. This creates seamless user experiences, helping people collaborate more effectively. You can work together from anywhere, on any device.

-
Hosted IP-PBX & Hosted Call Center
Hosted IP-PBX & Hosted Call Center
Streamlined Cloud Telephony with UC Capabilities
Simplify your company's voice and data operations with our comprehensive solutions. Many organizations juggle multiple vendors for their communication needs, leading to complexity with agreements, invoices, and contacts. Managing these can be a significant challenge. That's where we come in, offering top-notch business communication solutions featuring multi-tenant cloud telephony and Unified Communications as a Service (UCaaS) capabilities.

-
Voicebot, Chatbot
Voicebot, Chatbot
Elevate Your Business with Conversational AI
Voicebots and chatbots are transforming the way businesses interact with customers. These intelligent virtual assistants leverage conversational AI to provide seamless and efficient customer service and sales support. With 24/7 availability, they enhance automation, speed, and accessibility, leading to improved customer satisfaction and increased sales. Our expert team creates and deploys customized voicebot and chatbot solutions tailored to your business needs, empowering you to streamline your customer journey, reduce operational costs, and drive sales growth through intelligent automation.

-
Video Conferencing Hardware & Software
Video Conferencing Hardware & Software
Simple To Move, Simple To Use!
Our video conferencing solutions offer simplicity and flexibility, making collaboration effortless. Whether you're in the office or on the go, our hardware and software solutions ensure seamless communication. Here's what we offer:
Flexible Hardware: Our hardware solutions, including sound bars, video carts and stations, panoramic cameras, and accessories, are designed for easy mobility. Move them with ease and integrate them with your existing solutions for a hassle-free setup.
Comprehensive Software: We provide software for management and collaboration, optimizing the deployment of your devices. Our intuitive interface allows you to control and coordinate your video conferencing setup effortlessly.
Experience the convenience and efficiency of video conferencing with our hardware and software solutions. Streamline your communication and collaboration processes with ease, wherever you are.

-
Wireless Presentation & Collaboration
Wireless Presentation & Collaboration
Hassle-Free Collaboration & Content Sharing
Experience seamless collaboration and content sharing with our wireless presentation solutions. Whether you're using any video solution platform, our technology ensures smooth integration. Simply walk into the room, and your laptop automatically connects to room cameras, speakerphones, and sound bars. Get started within seconds, without the hassle of cables or setup. Save time and focus on what matters most – productive meetings and collaboration.

-
Intreractive display screens
Intreractive display screens
Connect with Your Audience!
Experience the power of interactive displays that transcend traditional presentations. Our interactive display screens revolutionize digital collaboration, elevate modern conferencing, enable seamless remote working, and enhance productivity and training outcomes. With intuitive touch capabilities and dynamic multimedia features, our interactive displays transform passive viewing into engaging experiences. Whether you're conducting a brainstorming session, delivering a presentation, or hosting a virtual meeting, our interactive screens empower you to captivate your audience and foster meaningful interactions. Unlock the potential of interactive technology to communicate ideas, share information, and drive collaboration like never before. Elevate your presentations, empower your team, and connect with your audience on a whole new level with our interactive display screens.

-
Microsoft Team Rooms
Microsoft Team Rooms
Empower Your Collaboration With Microsoft Team Rooms
Experience the future of hybrid work with our Microsoft Teams certified solutions. From boardrooms to home offices, our range of pro-grade audio and video products ensures exceptional collaboration experiences with Microsoft Teams, regardless of your work environment.

-
Audio Visual (AV)
Audio Visual (AV)
Solutions That Bring Everyone Together
Our Audio Visual (AV) design and installation solutions seamlessly integrate into various AV platforms, providing advanced capabilities for a wide range of environments. In conference rooms and meeting spaces, our AV systems enhance collaboration with high-quality audio and video solutions. Connected classrooms benefit from interactive learning environments, while auditoriums deliver impactful presentations and events. Sports arenas engage audiences with dynamic visual displays and clear audio, and command & control centers ensure efficient operations with reliable AV systems. Experience the power of integrated AV solutions that bring people together and transform your spaces.

-
Executive Boardrooms & Halls
Executive Boardrooms & Halls
Elevate Your Meeting Experience with Executive Boardrooms and Halls
In executive boardrooms and halls, important decisions are made and collaborations are nurtured. At our facilities, we offer comprehensive solutions to enhance your meeting experience and drive success. Our executive boardrooms and halls are equipped with state-of-the-art audio, camera, and video applications, ensuring seamless communication during video calls. With our built-in software, integrated with complete room solutions, joining a meeting is effortless. Simply click the controller, and you're ready to connect, without the need for your own PC or Mac. Experience rich connections and better collaborations in our executive boardrooms and halls, where every detail is designed to facilitate productivity and success.

-
Accessories & Peripherals
Accessories & Peripherals
Perfect Your Workspace
As remote and hybrid work becomes increasingly prevalent, there's a growing need for solutions that facilitate new forms of collaboration and co-creation. Our range of accessories and peripherals serves as the perfect complement to any workplace, enhancing efficiency and productivity in the modern work environment.

-
Omni Channel Contact center and Helpdesk
-
Surveillance & Physical Protection
Surveillance & Physical Protection
Protect Your People, Assets, and Data – From Every Angle
In today's world, comprehensive security goes beyond just firewalls and antivirus. Our Surveillance & Physical Protection solutions offer a holistic approach, safeguarding your personnel, software, hardware, and data from a range of physical threats and actions.

-
Surveillance & Physical Protection
Protect Your People, Assets, and Data – From Every Angle
In today's world, comprehensive security goes beyond just firewalls and antivirus. Our Surveillance & Physical Protection solutions offer a holistic approach, safeguarding your personnel, software, hardware, and data from a range of physical threats and actions.

-
-
Printing & Scanning
Printing & Scanning
Unleash Exceptional Prints at Unbeatable Costs
Revolutionize your printing and scanning experience with our cutting-edge technology. We leverage advancements like PrecisionCore™ to deliver impeccable quality for all your documents, all while minimizing waste and keeping costs remarkably low.

-
Business & Desktop Printers
Business & Desktop Printers
Enhance Workflow and Efficiency
Revolutionize your document management with our comprehensive selection of business and desktop printers. We offer a powerful range of features designed to streamline workflows, maximize productivity, and empower your team.
-
Label Printers
Label Printers
Empower Your Business with On-Demand Labeling Solutions
Transform your packaging and labeling processes with the power of in-house label printing. We offer a comprehensive range of label printers designed to empower businesses of all sizes – from SMEs to large enterprises – to unlock a world of benefits and boost their bottom line.

-
Handheld Printers
Handheld Printers
Unleash Printing Freedom
Imagine printing on the go, effortlessly. 247.Tech introduces a revolutionary solution – handheld printers. These innovative tools combine cutting-edge technology with portability, driving your business to new heights of productivity, convenience, and efficiency.

-
Document Scanners
Document Scanners
Empower Your Workflow
Elevate your document management with our comprehensive range of engineering-grade scanners. These compact and space-saving solutions are designed to revolutionize the way you handle technical drawings, blueprints, and schematics.

-
Barcode & RFID Scanners
Barcode & RFID Scanners
Empower Your Inventory: Unleash the Power of Barcode & RFID Scanners
Take control of your inventory with our comprehensive range of barcode and RFID scanners. These innovative tools place the power of instantaneous identification and data capture at your fingertips, offering a revolutionary approach to inventory management.
-
Print management system
Print management system
Unleash Control, Empower Efficiency: Print Management with 247.Tech
Take control of your printing costs and empower a more efficient workflow with a robust Print Management System from 247.Tech. Our software solutions are designed to optimize high-volume printing, streamlining processes, and maximizing savings for your business.
-
Document management system
Document management system
Streamline Your Workflow and Slash Printing Costs
Tired of paper overload and rising printing costs? Our Document Management System (DMS) lets you access, track, and edit documents from anywhere, while also keeping edit history for complete control. Securely upload and collaborate digitally, reducing printing and waste for a greener, more efficient workflow.

-
Consumables & Cartridges
Consumables & Cartridges
Unveiling Unmatched Performance: Your Source for Premium Consumables & Cartridges
Experience printing excellence with our curated selection of high-quality consumables and cartridges. Designed for seamless compatibility with industry-leading printing brands, our products deliver unparalleled results, ensuring flawless durability and unwavering reliability.

-
Business & Desktop Printers
-
Enterprise Mobility
Enterprise Mobility
Unlock Your Workforce Potential, Anytime, Anywhere
Say goodbye to the confines of the traditional office and hello to Enterprise Mobility. With our cutting-edge solutions, your team can work smarter, collaborate better, and achieve more—all from the palm of their hands. Whether in the office, on the road, or halfway around the world, empower your workforce to stay connected, productive, and ahead of the curve. Experience seamless integration, enhanced communication, and unparalleled flexibility with our innovative mobility solutions designed to transform your business operations and drive success in the digital age.

-
Handheld Mobile Computers
Handheld Mobile Computers
Handheld Computers: Power In Your Palm
Take your business wherever you go with our cutting-edge handheld computers. Compact, powerful, and versatile, these devices bring the world to your fingertips. Whether you need to manage inventory, provide field service, operate in retail, or deliver healthcare, our sleek handheld computers empower your workforce to tackle tasks with speed and precision, anytime, anywhere. Featuring intuitive interfaces and robust capabilities, our handheld computers streamline operations, enhance efficiency, and drive success across various industries. Embrace the future of mobile computing and elevate your business performance with our state-of-the-art solutions.

-
Mobile Computers (PDA)
Mobile Computers (PDA)
Mobile Computing (PDA): Stay Connected Anywhere, Anytime
Experience instant communication and seamless operation no matter where you are with our mobile computing solutions. Our rugged mobile computers are built to withstand the demands of diverse environments, including warehouses, hospitals, and airports. From positive patient identification to accurate asset labeling and stock management, our devices deliver reliability and precision. Featuring toughened glass construction capable of withstanding concrete impact, our tablets ensure durability in challenging conditions. Operating on familiar and user-friendly Windows and Android systems, our tablets offer easy navigation and connectivity virtually anywhere. Stay productive and connected with our robust mobile computing solutions.

-
Handheld Printers
Handheld Printers
Handheld Printers: Printing Convenience Wherever You Are
Experience printing convenience on the go with our handheld printers. Whether you need to print labels, tags, or documents at the point of service or while on the move, our quality printers deliver reliable performance wherever you are. Designed for various industries including laboratories, pharmacies, warehouses, and logistics firms, our compact printers are built to withstand tough conditions. With advanced battery technology ensuring continuous power throughout the longest shifts, you can rely on our handheld printers to improve accuracy and efficiency in your operations.

-
Mobile Device Management (MDM)
Mobile Device Management (MDM)
Mobile Device Management: Ensuring Seamless Control
Experience seamless control over your IT and network infrastructure with our AI-powered Mobile Device Management (MDM) solutions. Our products offer comprehensive monitoring and management capabilities, providing you with full visibility into all your devices and networks. In today's data-driven business landscape, it's essential to have a platform that collects, processes, and correlates events occurring across your heterogeneous and hybrid IT environment. Our MDM solutions do just that, empowering you with powerful insights to drive business outcomes and ensure optimal performance across your organization.

-
Computers on Wheels
Computers on Wheels
Computers On Wheels: Mobility For Medical Staff
Experience unparalleled mobility with our Computers on Wheels solutions. These carts are designed to enable medical staff to carry everything they need directly to the bedside, ensuring efficient and effective patient care. Equipped with scanners to retrieve vital information, wristband label printers for patient specimen labeling, and medication administration tools, our Computers on Wheels provide healthcare professionals with convenient access to essential resources wherever they go. Say goodbye to stationary workstations and hello to enhanced mobility and productivity with our Computers on Wheels.

-
Handheld Mobile Computers
-
Software Development
Software Development
Solutions Built for Your Business Goals
Empower your operations and elevate the customer experience with software designed to address your unique needs.
Our team of passionate and experienced developers leverages cutting-edge technologies to craft web platforms, mobile applications, and complex systems that perfectly align with your industry and vision.

-
ERP, CRM, HRMS
ERP, CRM, HRMS
Effortless Efficiency: Streamline Operations with Integrated Business Management
Our comprehensive suite of business management solutions offers a single source of truth, empowering you to make informed decisions and achieve peak performance.
Reduce overhead, cut costs, and boost profitability. Our integrated systems streamline processes, eliminate redundancies, and enhance efficiency across all departments.

-
Enterprise Application Development
Enterprise Application Development
Streamline Workflows with Scalable Enterprise Applications
247.Tech crafts integrated, scalable enterprise applications designed to automate tasks, empower your workforce, and streamline workflows for both employees and clients.
Our focus? Agility, speed, and scalability. We develop solutions that adapt and grow alongside your business, ensuring you're equipped to handle future demands.

-
Mobile Application development
Mobile Application development
Unleash the Power of Mobility: Transform Your Vision into Reality
We bridge the gap between imagination and innovation in mobile application development. We empower businesses to craft captivating mobile experiences that seamlessly connect with employees, partners, and customers.
-
Software development outsourcing
Software development outsourcing
Chart a Course for Success
We possess the expertise and capacity to craft robust, scalable, and secure software solutions tailored to any operating system, browser, or device. Our team seamlessly blends industry-specific knowledge with cutting-edge advancements in information technology.

-
Productivity & Automation
Productivity & Automation
Reimagine Productivity with Automation
We unlock the transformative potential of automation, helping you craft a seamless synergy between human ingenuity and digital innovation. We help you deploy a digital workforce that streamlines repetitive tasks, frees up valuable human resources, and empowers your team to focus on strategic initiatives.
-
PDF & Document Solutions
PDF & Document Solutions
Unleash the Power of All-in-One PDF Solutions
We offer a powerful suite of PDF solutions designed to simplify your workflow. Effortlessly edit existing PDFs, streamline e-signing for legal validity, and share content seamlessly by exporting to various formats like Word or Excel. Imagine the time saved and the efficiency gained – that's the power we bring to your document management.

-
Corporate Performance Management
Corporate Performance Management
Reimagine Performance Management: Unleash the Power of Automation
Managing complex data and generating reports can be a time-consuming hassle. We offer a transformative solution: Corporate Performance Management (CPM) with built-in automation.

-
Robotic Process Automation
Robotic Process Automation
Unlock Efficiency with Robotic Process Automation
Welcome to the future of automation with Robotic Process Automation (RPA). Our cutting-edge technology empowers you to save time, boost productivity, and foster innovation by automating repetitive digital tasks and processes. With our robot automation engine, you can seamlessly bridge technology islands and transform disconnected processes into unified, automated digital operations. Say goodbye to manual inefficiencies and hello to streamlined workflows with RPA.
-
Aerial Monitoring & Data Acquisition (Drones)
Aerial Monitoring & Data Acquisition (Drones)
Elevate Your Projects with Aerial Monitoring and Data Acquisition
Experience a new level of project efficiency and accuracy with our Aerial Monitoring and Data Acquisition services. Our cutting-edge technology ensures that you enjoy precision, efficiency, and cost-effectiveness in every project phase. With high-standard analytics and insights, along with meticulous data acquisition and processing, we empower you to make informed decisions and achieve superior project outcomes. Trust us to elevate your projects with unparalleled accuracy and efficiency.
-
Digital Payments & Financial
Digital Payments & Financial
Unleash Efficiency and Opportunity with 247.Tech's Digital Financial Solutions
In today's rapidly evolving financial landscape, staying ahead of the curve is crucial. 247.Tech's digital payments and financial solutions empower businesses with the latest technologies, designed to streamline operations and unlock a wealth of new opportunities. Our comprehensive suite caters to a wide range of players, including financial institutions, banks, telecom operators, and more. We offer significant cost reductions while simultaneously creating exciting avenues for growth.

-
Core Banking Systems
Core Banking Systems
Core Banking Systems
Be future-ready with an agile, interconnected, and efficient banking model. Our core banking system designs will transform your banking functions through cloud-native, regulatory-compliant, and real-time decision-making capabilities. This platform addresses various banking functionalities, including retail, corporate, wealth, and payments, enabling you to drive customer loyalty. Embrace the future of banking with our innovative and comprehensive core banking solutions.

-
Mobile, Internet & Agency Banking
Mobile, Internet & Agency Banking
Seamless Mobile, Internet & Agency Banking Solutions
Experience branchless banking at its finest with our comprehensive suite of services. We offer fast, convenient, and secure banking solutions tailored to meet the needs of your customers. Enjoy seamless customer profile creation, dynamic electronic KYC management, real-time transactions, and effortless onboarding processes. With our innovative platform, you can provide exceptional banking services to your customers anytime, anywhere. Simplify banking for your customers and elevate their experience with our customizable solutions.

-
Payments & Transfers
Payments & Transfers
Streamlined Payments & Transfers
Experience seamless local and cross-border payments with our Payments & Transfers solution. We offer a cost-effective and cashless model for rolling out domestic and international remittance services. Our solution ensures full traceability and transparency, incorporating built-in KYC and anti-money laundering features to meet regulatory requirements. Simplify your payment processes while maintaining compliance and security standards with our comprehensive solution.

-
Partner Management
Partner Management
Streamline Your Partnership Operations with Dynamic Partner Automation
Welcome to our Partner Management solution, where we introduce the efficiency of Dynamic Partner Automation. Our comprehensive system empowers you to effortlessly guide, manage, track, and communicate with your partners. With our innovative platform, partners can seamlessly conduct monetary transactions for mobile money users, while also simplifying the process of sending agent and user notifications. Say goodbye to cumbersome manual processes and hello to streamlined partnership management with Dynamic Partner Automation.

-
ERP, CRM, HRMS
-
Cloud and Connectivity
Cloud and Connectivity
Cloud Connectivity: Powering Your Business With Speed And Security
Our cloud solutions are designed to run any application faster and more securely. We provide comprehensive services to help you migrate, build, and manage all your IT needs, from existing enterprise workloads to new cloud-native applications and data platforms. With our expertise, you can ensure a seamless transition to the cloud, leveraging advanced technology to enhance performance, security, and scalability. Embrace the future of IT with our robust cloud connectivity solutions.

-
Private cloud
Private cloud
Private Cloud: Dedicated Cloud Infrastructure
Meet all your security, business governance, and regulatory compliance requirements with our private cloud computing. If your business has dynamic or unpredictable computing needs that require direct control over your environments, this is the cloud solution for you. Our private cloud offers unparalleled flexibility, security, and performance, ensuring your critical data and applications are managed in a dedicated infrastructure tailored to your specific needs. Experience the benefits of a custom cloud environment designed to support your unique business operations and growth.

-
Public cloud
Public cloud
Public Cloud: Pay-Per-Use Simplicity
Experience the ease of creating, deploying, and managing applications across multiple clouds, on-premise, and at the edge with our public cloud solutions. Enjoy the flexibility of a pay-per-use model, allowing you to scale resources as needed without the hassle of managing physical infrastructure. Let us empower your business with the simplicity and efficiency of public cloud computing.

-
Internet & MPLS
Internet & MPLS
Internet & MPLS: Reliable Connectivity 24/7
Achieve robust and dependable connectivity for your organization, enabling seamless communication between sites and other locations. Our solutions empower you to prioritize packet delivery and encrypt highly sensitive traffic while efficiently managing communication with limited manpower. Trust us to deliver reliable connectivity solutions that ensure uninterrupted operations round the clock.

-
Cloud Migration and consultancy
Cloud Migration and consultancy
The Fastest, Lowest Cost Path To The Cloud
Simplify your cloud migration journey with our streamlined infrastructure and operations. Our unified compute, network, storage, and Kubernetes stack seamlessly operate across any cloud, data center, or edge location. This flexibility allows you to select the ideal cloud for each application, migrate without the need for recoding, and manage everything from a single operational layer. Experience the fastest and most cost-effective path to the cloud with our comprehensive migration and consultancy services.

-
Satellite Connectivity
Satellite Connectivity
Nothing is too Remote
Empower your remote business with seamless high-speed internet connectivity, even in locations where fiber, cable, and wired options are unavailable. Our satellite connectivity solution ensures that no location is too remote for your operations. Additionally, it serves as a backup connection to maintain continuity when wired connectivity goes down. Experience reliable connectivity wherever your business takes you.

-
SD-WAN, Site to Site VPN
SD-WAN, Site to Site VPN
Connect Your Team Securely
Our SD-WAN and Site-to-Site VPN solutions ensure your team can securely connect from anywhere. Whether working from home, a hotel, an airport, or a conference, they can access company resources with guaranteed security and reliability.

-
Backhaul PTP PTMP
Backhaul PTP PTMP
Next Level Long Range Connectivity
Bridge your network across sites with our customized point-to-point (PTP) and point-to-multipoint (PTMP) solutions. We provide the best radios and antennas for your needs, ensuring optimal throughput and minimal interference with advanced technology options like isolating shields or AirPrism. Experience robust, long-range connectivity tailored to your unique requirements.
-
Private cloud
-
Trainings
Trainings
Upskill Your Team. Stay Ahead of the Curve.
In today's rapidly evolving business landscape, continuous learning is key. Equip your employees with the latest skills and knowledge to thrive. 247 Tech offers a comprehensive suite of engaging and innovative corporate training programs, strategically designed to align with your specific business goals.

-
IT Trainings
IT Trainings
Master the Tech, Conquer Your IT Goals
From help desk fundamentals to enterprise-level device management, 247 Tech equips you with the skills to excel in any IT role. Our comprehensive training programs combine in-depth tutorials with practical exercises, ensuring you gain a solid foundation in core IT concepts.

-
Security & Cloud Trainings
Security & Cloud Trainings
Level Up Your Cloud & Security Expertise
Our security and cloud training programs cater to all experience levels. Whether you're seeking to bolster your personal knowledge of cloud security or upskilling your entire team at work, we have the perfect program for you.

-
Business Trainings
Business Trainings
Turn Your Business Dreams into Reality
Ready to launch your dream business or take your existing venture to the next level? 247.Tech's Business Training Programs offer a wealth of knowledge and practical strategies from industry veterans who've walked the path to success.

-
IT Trainings
-
Network Monitoring
- Industries

-
Telecom
Telecom
CONNECT THE WORLD
WITH UNMATCHED SPEED
The demands for high bandwidth, attractive value added services and uninterrupted connections are unending. To capture customer trust and competitive markets, Telecoms and ISPs are striving to deploy powerful new networks while monetizing investments across their infrastructure.

-
Internet Billing and Digital Bss
Internet Billing and Digital Bss
AUTOMATING PROCESSES, SIMPLIFYING COMPLEXITIES
Experience a complete suite of technology products for Telecoms and ISPs that offer customized business plans and new revenue-generating platform. 247 Tech brings you cutting-edge technology solutions designed to streamline your billing and bandwidth management, leaving you free to focus on what truly matters - delivering exceptional user experience.
-
Wi-Fi SMP and Monetization
Wi-Fi SMP and Monetization
IMPROVE COVERAGE AND MONETIZE DATA
Through gated access, the Wi-Fi SMP enables you to collect user data and create personalized offers for captive portal users. Quickly build personalized portal pages to match your branding, and geo-specific customization for location-based advertising, and more.

-
E-KYC
E-KYC
ADVANCED BIOMETRICS THAT SIMPLIFY YOUR CUSTOMER ACQUISITION PROCESS
The eKYC advanced biometric ensures digital interaction with your customers for identity verification and digital onboarding. This reduces the costs and bureaucratic procedures necessary in traditional KYC processes. Access both hardware and software that will enhance your process and ensure compliance with client onboarding policies and procedures.

-
Caching and Peering
Caching and Peering
GET THE ULTIMATE INTERNET ACCELERATION.
Use DNS Caching for faster response times for DNS queries, especially for frequently requested domain names. As a telecom speed and user experience are a priority with Caching and peering solutions your users will enjoy ultra-high-speed downloads, content sharing, and browsing. Beyond that our solution saves bandwidth therefore saving you real money.

-
CSP: Cloud Hosting
CSP: Cloud Hosting
LAUNCH YOUR OWN PUBLIC CLOUD
Your customers are moving to the cloud, be equipped to become their cloud provider of choice. Data localisation, latency & local currency billing problems are creating an immense opportunity to build a multi-million dollar in-country public cloud business. Enjoy IaaS, PaaS, SaaS, CSaaS, CPaaS, and hosted PBX

-
Digital Payments and Mobile Money
Digital Payments and Mobile Money
START THE TRANSFORMATION TOWARDS DIGITAL SERVICE PROVIDER.
Get high-end telecom solutions that cater to all your business needs as a telecom operator and service provider. The mobile wallet solution is a complete platform that allows mobile network operators (MNOs), and mobile virtual network operators (VNOs, to launch an electronic wallet tightly linked to their core systems. Start your journey to become a digital payments provider for your clients.

-
Infrastructure and Log Monitoring
Infrastructure and Log Monitoring
MONITOR AND MANAGE ALL YOUR IT ASSETS
Secure full visibility and control of all your IT and network infrastructure, with AI-powered monitoring and management products. Data is king in the Telecom industry, the NMS collects all the events that occur in your heterogeneous and hybrid IT infrastructure, process, correlate, and provide powerful insights to drive business outcomes.

-
IT Service Management and Delivery
IT Service Management and Delivery
REINVENT YOUR INTERNAL SERVICE DELIVERY.
The ITSM service enables quick and efficient ticketing and issue resolution for your IT team. Built on the ITIL framework, the It service desk is aligned towards the high demands on IT teams in the telecom industry. The processes, procedures, tasks and checklist are based on industry best practices.

-
Omni Channel Call Center
Omni Channel Call Center
ENHANCE YOUR CALL CENTRE PRODUCTIVITY, CUSTOMER ENGAGEMENT & EXPERIENCE (CX)
Build an efficient call centre that provides top-notch customer service. The omni channel technology unites Outbound, Inbound, and Blended voice processes. It brings all your communications channels together; social media, text messages, calls, and email. In addition, it delivers Interactive Voice Response (IVR), Recording, Quality Management, Comprehensive Reporting, and insights, CRM integration, and Administrative Capabilities.
The Omni channel call center empowers your business to increase sales, save money and improve customer satisfaction with one comprehensive solution!
-
Video Conferencing
Video Conferencing
EXPERIENCE IMMERSIVE VIRTUAL MEETINGS!
Enjoy life-like and immersive virtual or hybrid meetings no matter the video solution platform you are using. Get high resolution images, engaging meetings with smart, interactive displays and whiteboards, high quality sound and wireless presentations. Walk into the room, automatically connect your laptop to room cameras, speakerphones, and sound bars. Get started within seconds. No cables, no mess, no time to waste.

-
Cable and Network Testing
Cable and Network Testing
RUGGED, RELIABLE AND ACCURATE TEST INSTRUMENTS
Use the right testing and fault locator tools for telecom operators. These include; rugged installation and testing tools such as termination tools, fault locators, tone generators and telephone line test sets.
-
Field Operations
Field Operations
DRIVE EFFICIENCY AND BOOST PRODUCTIVITY
Improve customer satisfaction with a lower cost per interaction by keeping service representatives connected with colleagues, customers, management and the tools they use to satisfy customers across the supply chain. The field operations portfolio includes fleet management, asset management, Mobile GIS surveying and mapping, and workforce management.

-
Security & Protection
Security & Protection
ADAPT YOUR SECURITY STRATEGIES – DEFEND AGAINST ADVANCED THREATS AND ATTACKS.
With a unique combination of technologies and services – all underpinned by world-leading security intelligence, mitigate cyber-risk, detect different types of attacks at an earlier stage, deal with live attacks, and improve overall protection.

-
Networking, Computing & Storage
Networking, Computing & Storage
SCALABLE HIGH-PERFORMANCE TECHNOLOGY
Build software driven cloud networks for today’s datacenter, cloud and campus environments.
By using technology that enables software applications that deliver workflow automation, high availability, unprecedented network visibility and analytics and rapid integration with a wide range of third-party applications for virtualization, management, automation and orchestration services.

-
Wireless Connectivity
Wireless Connectivity
BUILD SEAMLESS, HIGH PERFORMANCE AND ROBUST CONNECTIONS
Expand into new markets and maximize customer satisfaction while minimizing costs. Your business can deliver multi-gigabit speeds for indoor and outdoor Wi-Fi applications and oversee the entire network with easy-to-use, centralized cloud management.
-
Printing and Scanning
Printing and Scanning
HIGH-QUALITY, LOW-COST TECHNOLOGY
Make everyday tasks easy with an expansive line-up of printers including continuous feed presses that provide over 100 meters-per-minute high-speed printing on paper rolls; sheet-fed presses that print on standard size paper; and large-format printers. Also enjoy state-of-the-art RFID and barcode scanners and document management systems that improve productivity and automation.

-
Queue Management System
Queue Management System
EFFICIENT OPERATIONS FOR SMOOTH CUSTOMER EXPERIENCE
Improve the waiting experience, gather service intelligence, and make data-driven decisions with a queue management system. The system covers everything from simple ticketing, self-check-in kiosk, and display solutions to a fully tailored customer journey platform that utilizes customer data.

-
Internet Billing and Digital Bss
-
HealthCare
HealthCare
ENABLING THE DELIVERY
OF EXCELLENT PATIENT CARE
At 247 we use systems to enable hospitals, pharmaceuticals and other healthcare institutions to offer the best care to their patients. The healthcare industry is always working to improve the care it provides to patients, enhance clinical research and protect the people providing medical care.

-
Clinical Mobility
Clinical Mobility
ACCESS THE INFORMATION YOU NEED ON THE GO
Our Clinical Collaboration Solutions enable you to connect instantly with colleagues, information and applications you need, from the patient's side. From computers on wheel, to rugged clinical smart phones and mobile computing, our solutions enable health care providers to offer excellent patient care on the move!
-
Patient Identification
Patient Identification
REDUCE PATIENT IDENTIFICATION ERRORS
Instil the confidence of knowing you are right with positive identification solutions. Implement patient identification solutions including printers, GSI compliant wrist bands and barcode scanners, that enable you to identify, track and manage all patient information.

-
Hospital Consumables
Hospital Consumables
COST-EFFECITVE, SUSTAINIBLE SUPPLY
Discover a range of essential healthcare consumables designed to streamline operations and ensure precision in the fast-paced healthcare environment. From printing consumables like labels, ribbons and barcode wristbands to medical consumable such as PPEs.

-
Real-time tracking and Locating
Real-time tracking and Locating
AUTOMATING VISIBILITY TO ASSET LOCATION
Track assets and locate patients and staff in real time. Gain visibility into your operation for actionable data driven insights by implementing Radio Frequency Identification (RFID) asset tracking and Real Time Locating Systems (RTLS) for better healthcare management and patient care.

-
Queue Management Solution
Queue Management Solution
IMPROVE OPERATIONAL EFFICIENCY AND PATIENT SERVICE
Improve patient satisfaction and staff productivity with queue management. It enables your healthcare providers to optimize patient flow, reduce wait times, and enhance overall operational efficiency. With real-time updates and intelligent routing, patients experience a seamless journey from check-in to consultation and/or admission. The user-friendly interface allows staff to monitor and manage queues effortlessly, ensuring a smooth and organized workflow within your hospital premises.

-
Software Development HMS
Software Development HMS
DIGITIZE YOUR HEALTHCARE DELIVERY
Experience the power of patient engagement, seamless service delivery whether pharmacy, radiology, ward, or lab, and a centralized command and monitoring platform. The HMS focuses on all customer touch points queue management, patient registration, appointment management, essential services like pharmacy, speech-to-text technology for faster service, and so much more.

-
IP Telephony
IP Telephony
CREATE POWERFUL BUSINESS CONNECTIONS
Streamline communications to improve quality of care for your patients. By removing the worry out of communications, you enable your medical professionals to focus on saving and improving the lives of those under their care.

-
Conference / Board Room Solutions (Telemedicine)
Conference / Board Room Solutions (Telemedicine)
RICH CONNECTIONS, BETTER COLLABORATION
Utilize integrated communication tools such as web and video conferencing, voice mail, wireless presentation, instant messaging and smart displays. They create seamless user experiences that help your health professionals work together more effectively; anywhere, and on any device.

-
High-speed Internet Access (Hsia) & Connectivity
High-speed Internet Access (Hsia) & Connectivity
EXPERIENCE UNMATCHED SPEED
The Healthcare Wi-Fi hotspot solution enables hospitals to offer swift and secured internet access to users. It effectively manages fair distribution of bandwidth, allows authenticated user traffic and systematic log of user surfing details. The appliances are available in different range of models by which small to large healthcare centres and hospitals can select the choice of appliance, according to your user network needs.

-
Cybersecurity
Cybersecurity
SHIELDING PATIENT PRIVACY, ONE BYTE AT A TIME.
Cyber security is one the most important and integral parts of today’s advanced healthcare IT network infrastructure. We work to ensure your patients’ privacy is never threatened.
Our cybersecurity products and services ensure that all your surfaces are protected through advanced AI technology and an expert team to prevent and handle malicious activities like ransomware, phishing, malware attacks and many more.

-
Physical Security
Physical Security
HEALTHCARE'S FRONTLINE DEFENSE
Prioritize the security of personnel, software and hardware networks as well as data from damage or loss by physical events and actions. From access control to surveillance and video management systems ensure all your people, processes and technologies are safeguarded.

-
IT Infrastructure
IT Infrastructure
SCALABLE, HIGH-PERFORMANCE TECHNOLOGY
Implement infrastructure that ensures operational efficiency, agility, and scale for hybrid cloud infrastructure. Install solutions that enable a set of software applications which deliver workflow automation, high availability, unprecedented network visibility and analytics and rapid integration with a wide range of third-party applications for virtualization, management, automation and orchestration services.

-
Clinical Mobility
-
Hospitality
Hospitality
CREATE UNFORGETTABLE
EXPERIENCES FOR YOUR GUESTSThe hospitality industry is increasingly competitive and serves a very savvy customer base. We aim to keep you at the top of your niche with technology designed for your unique needs.
-
High Speed Internet Access (HSIA)
High Speed Internet Access (HSIA)
TAKE YOUR GUEST EXPERIENCE TO THE NEXT LEVEL!
Hotel guests today demand high speed internet access. The industry is faced with network congestion, connectivity hassles, unsecure access to their network, lack of guest surfing logs and enabling guest ease when logging in. The Internet Access Management System is specially designed to provide excellent Internet services to hotel guests. It is a fully customizable and highly flexible plug-and-play solution. An industry leading HSIA platform with attractive captive portal functionalities and integrated with leading property management systems (PMS).

-
IP Telephony and Communication
IP Telephony and Communication
INTEGRATED COLLABORATION THAT BRINGS PEOPLE TOGETHER IN ONE EXPERIENCE
Implement a Unified communications suite that delivers integration of communication tools such as IP telephony, web and video conferencing, voice mail, mobility, desktop sharing, instant messaging and presence. It creates seamless user experiences that help people work together more effectively anywhere, and on any device.

-
Conference Room Solution
Conference Room Solution
RICH CONNECTIONS, BETTER COLLABORATION
Create superior meeting experiences for your executives and your clients. Take your virtual meetings to a life-like level that enhance deeper conversations and collaborative experiences for your conferences and workshops. Buy or lease state-of the-art solutions for your boardrooms, events and workshops

-
Printing and Scanning
Printing and Scanning
HIGH QUALITY, LOW COST
As a hotel, you have different printing requirement to enhance workflow for your staff and create convenience for your guests. These include food labels for your buffets, welcome cards for your guests, receipts and so much more. It requires printers that deliver a blend of quality, speed and convenience. Enjoy robust printing and scanning units that can provide clear, high-quality cards, labels and documents, with upfront purchase, rental, or leasing options

-
Property Management Software
Property Management Software
HOSPITALITY REDEFINED: SMART SOLUTIONS FOR SMART HOTELS
Easy-to-use property management with a clear, consistent user experience. Enjoy a complete range of software solutions developed for the complexity and inter-connectedness of the various functions in hospitality. Simplify and streamline your business process for quality customer experiences using a platform built for stability, scale, and innovation.

-
Cybersecurity
Cybersecurity
360 COVERAGE
247 Tech provides 360 cybersecurity infrastructure to ensure complete protection of your network. The expert team of cybersecurity professionals ensures proper integration of all your solutions so that your IT team can manage everything from one dashboard.

-
Physical Security
Physical Security
DIGITAL SECURITY EVERYWHERE YOU NEED IT
Protect your guests and secure assets with smart access control, real-time surveillance, and loss prevention technology. Implement core techniques, smart terminals, and software platforms based on smart entrance & and exit to enhance security and convenience at your premises.

-
Back Up and Disaster Recovery
Back Up and Disaster Recovery
EFFICIENT & SECURE BACKUP & RECOVERY
Enjoy industry-leading backup, recovery and data security solution for all your workloads, both on-premises and in the cloud. Eliminate downtime with Instant Recovery and stay safe from cyberthreats with native immutability and tested backups, all from a software-defined, hardware-agnostic solutions. The backup and disaster recovery enables; instant recovery, enterprise applications, offsite replication and data recovery anywhere.

-
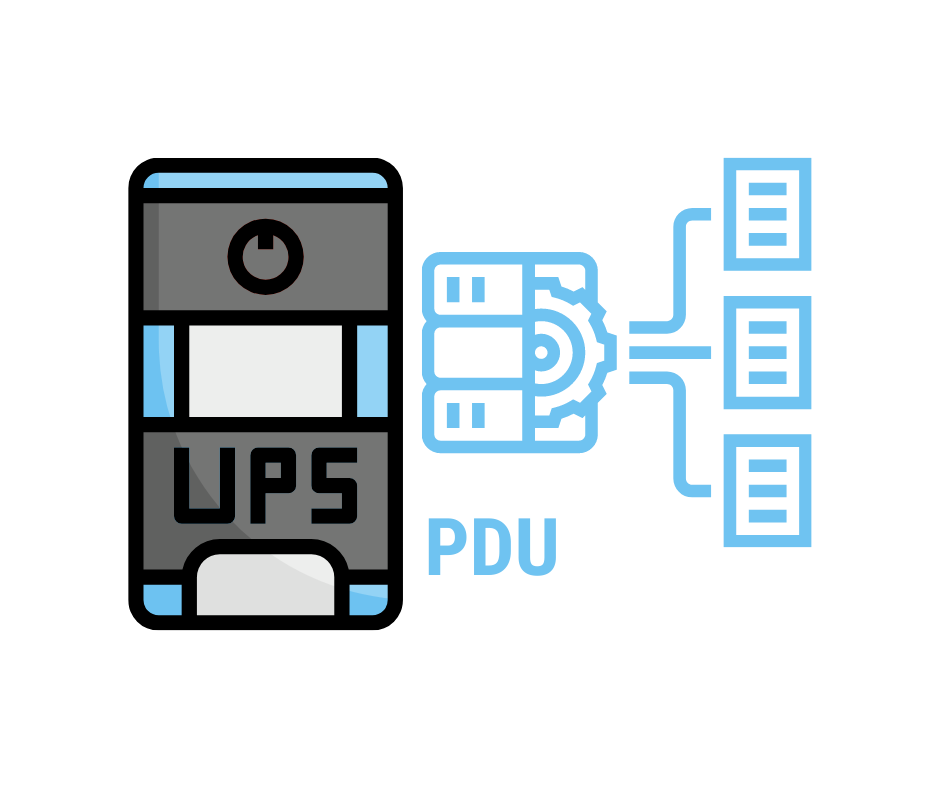
IT Power Solutions
IT Power Solutions
NO MORE DOWNTIME
Unlock continuous and stable supply of electricity to critical IT infrastructure. Using a wide range of technologies and systems from Uninterruptible Power Supplies (UPS) that protect against power interruptions to energy-efficient inverters that optimize power conversion, keep your digital world running smoothly.
-
Networking, Storage and Computing
Networking, Storage and Computing
SCALABLE HIGH-PERFORMANCE AND RESILIENT TECHNOLOGY
Implement high performance IT infrastructure that runs all applications and your network. This ensures uninterrupted and quality services for your staff and your guests.

-
Hospitality IPTV
Hospitality IPTV
SEAMLESS, ENGAGING ENTERTAINMENT
In the dynamic world of hospitality, there is a need for seamless and engaging entertainment. Offer your guests a wide array of content at their fingertips with state-of-the-art IPTV. From on-demand movies and streaming services to personalized guest information and room service ordering. The hospitality IPTV system ensures your guests stay entertained and informed throughout their stay.

-
Guest Room Automation and Lighting Automation
Guest Room Automation and Lighting Automation
STEP INTO THE FUTURE
Step into the future of guest comfort and convenience with cutting-edge Smart Guest Room Automation. This provides a seamless and personalized experience from the moment your guests check-in and immediately sets the stage for a perfect stay.

-
High Speed Internet Access (HSIA)
-
Public Sector
Public Sector
POWERING ENGAGING
AND CITIZEN-CENTRIC SERVICES
The public sector is constantly striving to create positive societal outcomes while navigating sensitive issues such as understanding the needs of the people, data security and privacy.

-
Cybersecurity
Cybersecurity
360 COVERAGE
Cyber security is one the most important and integral parts of today’s advanced IT network infrastructure. Our cybersecurity products and services ensure that all your surfaces are protected through advanced AI technology and an expert team. We prevent and handle malicious activities like ransomware, phishing, malware attacks and many more.

-
Unified Communication and Collaboration
Unified Communication and Collaboration
CREATE POWERFUL BUSINESS CONNECTIONS
Create superior meeting experiences for your executives and stakeholders. Take your virtual meetings to a life-like level that enhance deeper conversations and collaborative experiences for your conferences and workshops. Buy or lease state-of the-art solutions for your boardrooms, events and workshops
-
Video Conferencing
Video Conferencing
EXPERIENCE IMMERSIVE VIRTUAL MEETINGS!
Enjoy life-like and immersive virtual or hybrid meetings no matter the video solution platform you are using. Get high resolution images, engaging meetings with smart, interactive displays and whiteboards, high quality sound and wireless presentations. Walk into the room, automatically connect your laptop to room cameras, speakerphones, and sound bars. Get started within seconds. No cables, no mess, no time to waste.

-
Queue Management System
Queue Management System
REDEFINE YOUR EFFICIENCY FOR SMOOTH CUSTOMER EXPERIENCE
Improve citizen satisfaction and staff productivity with queue management. It enables your public offices to optimize customer flow, reduce wait times, and enhance overall operational efficiency. With real-time updates and intelligent routing, citizens experience a seamless journey from check-in to consultation and service delivery. The user-friendly interface allows staff to monitor and manage queues effortlessly, ensuring a smooth and organized workflow within your premises.

-
Service Delivery –ITSM
Service Delivery –ITSM
EMPOWERING YOUR OPERATIONS WITH ITSM EXPERTISE
Our ITSM service enables quick and efficient ticketing and issue resolution for your IT team. Enhance your team's productivity and reinvent your internal service delivery. Built on the ITIL framework, the It service desk is aligned towards the critical demands on It teams in the public sector. The processes, procedures, tasks and checklist are based on industry best practices.

-
Network and Infrastructure Monitoring
Network and Infrastructure Monitoring
MONITOR AND MANAGE ALL YOUR IT ASSETS
Secure full visibility and control of all your IT and network infrastructure, with AI-powered monitoring and management products. Data is king, the NMS collects all the events that occur in your heterogeneous and hybrid IT infrastructure, process, correlate, and provide powerful insights to drive business outcome

-
Printing & Scanning
Printing & Scanning
HIGH QUALITY, LOW COST
Businesses have different printing and scanning requirements to enhance workflow for staff and create convenience for clients. These include document scanning, document management, receipt printing and so much more. This requires printers that deliver a blend of quality, speed and convenience. Enjoy robust printing and scanning units that can provide clear, high-quality cards, labels and documents, with upfront purchase, rental, or leasing options

-
Physical Security & Access Control
Physical Security & Access Control
DIGITAL SECURITY, WHEREVER YOU NEED IT
Prioritize the security of personnel, clients, software and hardware networks as well as data from damage or loss by physical events and actions. From access control to surveillance and video management systems we ensure all your people, processes and technologies are safeguarded.

-
IT Infrastructure
IT Infrastructure
SCALABLE, HIGH-PERFORMANCE TECHNOLOGY
Implement infrastructure that ensures operational efficiency, agility, and scale for hybrid cloud infrastructure. Install solutions that enable a set of software applications which deliver workflow automation, high availability, unprecedented network visibility and analytics and rapid integration with a wide range of third-party applications for virtualization, management, automation and orchestration services.

-
Cybersecurity
-
BFSI
BFSI
SMART FINANCIAL SERVICES
AT THE TIP OF YOUR HANDSThe Banking, Finance and Insurance industry is rapidly developing, employing new technologies to move aggressively and strategically leverage productivity, become technology driven and increase reach.
-
Service Delivery –ITSM
Service Delivery –ITSM
EMPOWERING BANKING OPERATIONS WITH ITSM EXPERTISE
Our ITSM service enables quick and efficient ticketing and issue resolution for your IT team. Enhance your team's productivity and reinvent your internal service delivery. Built on the ITIL framework, the IT service desk is aligned towards the critical demands on IT teams in the finance sector. The processes, procedures, tasks and checklist are based on industry best practices.

-
Omni Channel Contact Center
Omni Channel Contact Center
ENHANCE YOUR CALL CENTRE PRODUCTIVITY, CUSTOMER ENGAGEMENT & EXPERIENCE (CX)
Build an efficient call centre that provides top-notch customer service. The omni channel technology unites Outbound, Inbound, and Blended voice processes. It brings all your communications channels together; social media, text messages, calls, and email. In addition, it delivers Interactive Voice Response (IVR), Recording, Quality Management, Comprehensive Reporting, and insights, CRM integration, and Administrative Capabilities.
The Omni channel call center empowers your business to increase sales, save money and improve customer satisfaction with one comprehensive solution!

-
Queue Management System
Queue Management System
BANKING EFFICIENCY REDEFINED FOR SMOOTH CUSTOMER EXPERIENCE
Improve customer satisfaction and staff productivity with queue management. It enables your banking staff to optimize customer flow, reduce wait times, and enhance overall operational efficiency. With real-time updates and intelligent routing, clients experience a seamless journey. The user-friendly interface allows staff to monitor and manage queues effortlessly, ensuring a smooth and organized workflow within your premises.

-
Network and Infrastructure Monitoring
Network and Infrastructure Monitoring
MONITORING BANKING'S DIGITAL BACKBONE
Secure full visibility and control of all your IT and network infrastructure, with AI-powered monitoring and management products. Data is king in the financial sector, the NMS collects all the events that occur in your heterogeneous and hybrid IT infrastructure, process, correlate, and provide powerful insights to drive business outcome.
-
Advanced Cybersecurity
Advanced Cybersecurity
WHERE THREATS MEET THEIR MATCH: ADVANCED CYBER DEFENSE.
Cyber security is one the most important and integral parts of today’s advanced IT network infrastructure. Our cybersecurity products and services ensure that all your surfaces are protected through advanced AI technology and an expert team we prevent and handle malicious activities like ransomware, phishing, malware attacks, and many more.

-
Physical Security & Access Control
Physical Security & Access Control
MODERNIZED AND ENHANCED SAFETY
Prioritize security of personnel, software and hardware networks as well as data from damage or loss by physical events and actions. Be aware and enjoy control over who has access to your premises. Enable role-based access for different areas and assets on your premises. Save time and resources caused by natural disasters, burglary, theft or vandalism and get visual evidence to identify the culprit and their tactics.

-
Banking Software Suite
Banking Software Suite
BUILD A DIGITAL FINANCIAL ECOSYSTEM
Implement digital financial solutions that are the latest technologies to deliver best-in-class services that drastically drive down the costs, while unlocking new business opportunities for financial institutions. The suite includes cutting-edge financial services such as e-KYC, core banking, mobile and agency banking to simplify online transactions and drive financial inclusion for the unbanked and underbanked around Africa.

-
Printing & Scanning
Printing & Scanning
HIGH QUALITY, LOW COST
Financial institutions have different printing and scanning requirements to enhance workflow for staff and create convenience for clients. These include cheque scanning, document management, receipt printing and so much more. This requires printers that deliver a blend of quality, speed and convenience. Enjoy robust printing and scanning units that can provide clear, high-quality cards, labels and documents, with upfront purchase, rental, or leasing options

-
Boardroom Solutions
Boardroom Solutions
RICH CONNECTIONS, BETTER COLLABORATION
We deliver integrated communication tools such as web and video conferencing, voice mail, wireless presentation, instant messaging and smart displays. They create seamless user experiences that help banking and finance professionals work together more effectively; anywhere, and on any device

-
IT Infrastructure
IT Infrastructure
SCALABLE, HIGH-PERFORMANCE TECHNOLOGY
Implement infrastructure that ensures operational efficiency, agility, and scale for hybrid cloud infrastructure. The infrastructure enables a set of software applications that deliver workflow automation, high availability, unprecedented network visibility and analytics and rapid integration with a wide range of third-party applications for virtualization, management, automation and orchestration services.

-
Service Delivery –ITSM
-
Education
Education
THE CLASSROOM
OF THE FUTUREThe way that learning in delivered is changing. The new advances come with new responsibilities for educators to evolve their classrooms to meet the evolution of technology and the transfer of knowledge today.

-
Digital Classrooms & Board Room Solutions
Digital Classrooms & Board Room Solutions
BUILD SMART CLASROOMS
Foster opportunities for teaching and learning by integrating learning technology, such as computers, audience response technology, assistive listening devices, smart displays, auditorium projectors, and video conferencing.

-
Physical Security Solution
Physical Security Solution
DIGITAL SECURITY, WHEREVER YOU NEED IT
Prioritize the security of personnel, students, parents, software and hardware networks as well as data from damage or loss by physical events and actions. From access control to surveillance and video management systems ensure all your people, processes and technologies are safeguarded.

-
Cybersecurity
Cybersecurity
SAFEGUARDING THE DIGITAL CLASSROOM
Cyber security is one the most important and integral parts of today’s advanced IT network infrastructure. Our cybersecurity products and services ensure that all your surfaces are protected through advanced AI technology and an expert team we prevent and handle malicious activities like ransomware, phishing, malware attacks, and many more.
-
Printing & Scanning
Printing & Scanning
HIGH QUALITY, LOW COST
Education institutions have different printing and scanning requirements to enhance workflow for staff and create convenience for teachers and students. These include document scanning, document management, printing teaching material, receipt printing and so much more. This requires printers that deliver a blend of quality, speed and convenience. Enjoy robust printing and scanning units that can provide clear, high-quality cards, labels and documents, with upfront purchase, rental, or leasing options

-
High Speed Internet Access (Hsia)
High Speed Internet Access (Hsia)
EXPERIENCE UNMATCHED SPEED
Provide regulated internet access to users in classrooms, libraries and Wi-Fi hotspot access in dorms through extensive bandwidth controls over excessive usage. Enjoy cost-efficient comprehensive solution that offers all the advance facilities and features in single platform with single point of contact for technical support.

-
Unified Communication and Collaboration
Unified Communication and Collaboration
CREATE POWERFUL CONNECTIONS
Enhance learning with superior communication technology. The UC solutions creates superior engagement between teachers and their students, the school and parents with a single view from multiple channels. They enhanced insight and visibility for all communication and enable effective and targeted learning campaigns.

-
Education Management Software Solution
Education Management Software Solution
MANAGE YOUR CAMOUS EFFORTLESSLY
Enjoy a complete range of software solutions developed for the complexity and inter-connectedness of the various functions in a school campus. Simplify and streamline your business process for quality student experiences and maximum security.

-
Campus IT Infrastructure
Campus IT Infrastructure
SCALABLE, HIGH-PERFORMANCE TECHNOLOGY
Implement infrastructure that ensures operational efficiency, agility, and scale for hybrid cloud infrastructure. Instal infrastructure that enables a set of software applications that deliver workflow automation, high availability, unprecedented network visibility and analytics and rapid integration with a wide range of third-party applications for virtualization, management, automation and orchestration services.

-
Digital Classrooms & Board Room Solutions
-
SME & Enterprise
SME & Enterprise
Edge out competition! Build a fully automated business...
Digitized Enterprises & SMEs reduce transaction costs by providing better and quicker access to information, communication, and integration with global markets enhancing their scope to facilitate the best services with sustainable growth.
-
Cybersecurity
Cybersecurity
360 COVERAGE
Cyber security is one the most important and integral parts of today’s advanced IT network infrastructure.Our cybersecurity products and services ensure that all your surfaces are protected through advanced AI technology and an expert team we prevent and handle malicious activities like ransomware, phishing, malware attacks and many more.

-
Unified Communication and Collaboration
Unified Communication and Collaboration
CREATE POWERFUL BUSINESS CONNECTIONS
The business world today is hybrid. More meetings are held remotely than on premises. Take your communications to the next level with a bouquet of communication products that offer excellent audio-visual solutions that allow you to have clear and impactful conversations.

-
Video Conferencing
Video Conferencing
EXPERIENCE IMMERSIVE VIRTUAL MEETINGS!
Enjoy life-like and immersive virtual or hybrid meetings no matter the video solution platform you are using. Get high resolution images, engaging meetings with smart, interactive displays and whiteboards, high quality sound and wireless presentations. Walk into the room, automatically connect your laptop to room cameras, speakerphones, and sound bars. Get started within seconds. No cables, no mess, no time to waste.

-
Printing & Scanning
Printing & Scanning
HIGH QUALITY, LOW COST
Businesses have different printing and scanning requirements to enhance workflow for staff and create convenience for clients. These include document scanning, document management, receipt printing and so much more. This requires printers that deliver a blend of quality, speed and convenience. Enjoy robust printing and scanning units that can provide clear, high-quality cards, labels and documents, with upfront purchase, rental, or leasing options

-
Physical Security & Access Control
Physical Security & Access Control
DIGITAL SECURITY, WHEREVER YOU NEED IT
Prioritize the security of personnel, clients, software and hardware networks as well as data from damage or loss by physical events and actions. From access control to surveillance and video management systems we ensure all your people, processes and technologies are safeguarded.

-
Software Development
Software Development
MANAGE YOUR BUSINESS EFFORTLESSLY
Reduce overheads and cut costs by making business processes more efficient using tailor-made business management software that gives you a single source of trust. This reducing the amount of capital spent on processes, and works to increase profits by producing

-
IT Infrastructure
IT Infrastructure
SCALABLE, HIGH-PERFORMANCE TECHNOLOGY
Implement infrastructure that ensures operational efficiency, agility, and scale for hybrid cloud infrastructure. Instal infrastructure that enables a set of software applications that deliver workflow automation, high availability, unprecedented network visibility and analytics and rapid integration with a wide range of third-party applications for virtualization, management, automation and orchestration services.

-
Cybersecurity
-
Manufacturing
Manufacturing
POWERING EFFICIENT AND
SUSTAINABLE MANUFACTURING
The Manufacturing industry is seeing demand and transformation unlike before powered by advanced technologies, IOT, data-driven equipment's and seamless integration.
-
Software Solution for FMCG
Software Solution for FMCG
A UNIQUE APPROACH TO ANALYSIS, PROCUREMENT AND DATA MANAGEMENT
Clean your inventory data using a comprehensive business process aligning practice and technology components to provide sound data on materials, suppliers, products, inventory, and cost. Handle all inventory, expense order management, and consolidate all indirect material across multiple sites within a single system.

-
IP Telephony
IP Telephony
CREATE POWERFUL BUSINESS CONNECTIONS
Streamline communications to improve quality of care for your customers. By removing the worry out of communications, you enable your factory workers to focus on producing quality products

-
Cybersecurity
Cybersecurity
360 COVERAGE
Cyber security is one the most important and integral parts of today’s advanced IT network infrastructure. Our cybersecurity products and services ensure that all your surfaces are protected through advanced AI technology and an expert team we prevent and handle malicious activities like ransomware, phishing, malware attacks and many more.

-
Board Room Solutions
Board Room Solutions
RICH CONNECTIONS, BETTER COLLABORATION
We deliver integrated communication tools such as web and video conferencing, voice mail, wireless presentation, instant messaging and smart displays. They create seamless user experiences that help your staff work together more effectively; anywhere, and on any device.

-
IT Infrastructure
IT Infrastructure
SCALABLE, HIGH-PERFORMANCE TECHNOLOGY
Implement infrastructure that ensures operational efficiency, agility, and scale for hybrid cloud infrastructure. Instal infrastructure that enables a set of software applications that deliver workflow automation, high availability, unprecedented network visibility and analytics and rapid integration with a wide range of third-party applications for virtualization, management, automation and orchestration services.

-
Physical Security
Physical Security
YOUR FRONTLINE DEFENSE
Prioritize the security of personnel, software and hardware networks as well as data from damage or loss by physical events and actions. From access control to surveillance and video management systems we ensure all your people, processes and technologies are safeguarded.

-
IT Power Solutions
IT Power Solutions
NO MORE DOWNTIME
Enjoy continuous and stable supply of electricity to critical IT infrastructure. Using a wide range of technologies and systems from Uninterruptible Power Supplies (UPS) that protect against power interruptions to energy-efficient inverters that optimize power conversion, keep your digital world running smoothly

-
Fire Detection and Suppression
Fire Detection and Suppression
SECURE YOUR DATA
The combination of fire detection and suppression delivers the best result to save your data center infrastructure and factory in the event of fire. It is specifically designed to sense heat and automatically start the process of suppression.
-
Software Solution for FMCG
-
Transport Logistics & Warehousing
Transport Logistics & Warehousing
DELIVER ON TIME
Technology has impacted a lot on 3PL Industry in last 10 years. From simple transportation and warehousing to fully equipped, specialized and digitized transportation and warehousing management. Transparency across all the levels of load tracking to freight visibility has become a basic demand.

-
Inventory and Asset Management
Inventory and Asset Management
STREAMLINE DAY-TO-DAY MANAGEMENT.
Inventory and asset management that gives you unprecedented visibility into every corner of your operation - to make smarter, more informed decisions, and ensure flawless fulfillment. This enables you to know the current status and location of all assets for greater productivity and cycle count efficiency.
-
Printing
Printing
HIGH QUALITY, LOW COST
Invest in printers with features that help your business improve document-related processes. From adding convenience for employees to reducing operating costs and improving productivity, your business can consolidate its print operations with multifunction printer systems.

-
Scanning
Scanning
DESIGNED FOR ALL YOUR DATA CAPTURE NEEDS
Ultra-rugged scanners, built for the unique challenges of transport, logistics and warehouse tasks. These scanners stand up to harsh conditions, read at astonishing lengths and speeds, and give workers nonstop, full-shift power

-
PDA and Rugged Tabs
PDA and Rugged Tabs
OPTIMISE PRODUCTIVITY AND SERVICE WITH SUPERIOR COMMUNICATION
Provide your workforce with reliable, rugged voice and data communication devices that increase productivity and promote safe and efficient workflows.

-
MDM
MDM
SECURE UNIFIED ENDPOINT MANAGEMENT
Spend less time and effort managing and securing traditional and mobile endpoints. Implement the only UEM solution that integrates natively with a leading next-gen endpoint security platforms, and supports management of Windows 10, macOS, iOS, and Android devices.

-
Physical Security
Physical Security
YOUR FRONTLINE DEFENSE
Prioritize the security of personnel, software and hardware networks as well as data from damage or loss by physical events and actions. From access control to surveillance and video management systems we ensure all your people, processes and technologies are safeguarded.
-
RFID
RFID
UNMATCHED ACCURACY THAT ELEVATES EVERY SYSTEM, DEVICE, TAG AND WORKER.
From warehouses and loading docks to indoor customer-facing and carpeted environments, use a range of RFID technology such as readers and RFID-enabled devices to help you achieve maximum visibility into your enterprise and customers assets.

-
Connectivity
Connectivity
RELIABLE CONNECTIVITY 247
Get robust and reliable connectivity for your organization which allows you to communicate between sites and every other location.
-
Wireless Connectivity
Wireless Connectivity
ENABLE SEAMLESS MOVEMENT
With the help of Wireless connectivity, your business can track its fleet's location, monitor vehicle diagnostics, and collect real-time data on fuel consumption, engine performance, and maintain requirements.
-
Software Applications
Software Applications
MANAGE YOUR BUSINESS EFFORTLESSLY
Business management solutions that give you a single source of trust system with components that focus on reducing overheads and cutting costs by making business processes more efficient. This reduces the amount of capital spent on processes, and works to increase profits by producing greater sales volume

-
Cybersecurity
Cybersecurity
360 COVERAGE
Cyber security is one the most important and integral parts of today’s advanced IT network infrastructure. Our cybersecurity products and services ensure that all your surfaces are protected through advanced AI technology and an expert team we prevent and handle malicious activities like ransomware, phishing, malware attacks and many more.

-
Communicaiton
Communicaiton
INTEGRATED COLLABORATION THAT BRINGS PEOPLE TOGETHER IN ONE EXPERIENCE
We deliver integrated communication tools such as web and video conferencing, voice mail, wireless presentation, instant messaging and smart displays. They create seamless user experiences that help your staff work together more effectively; anywhere, and on any device.

-
IT Infrastructure
IT Infrastructure
SCALABLE, HIGH-PERFORMANCE TECHNOLOGY
Implement infrastructure that ensures operational efficiency, agility, and scale for hybrid cloud infrastructure. Instal infrastructure that enables a set of software applications that deliver workflow automation, high availability, unprecedented network visibility and analytics and rapid integration with a wide range of third-party applications for virtualization, management, automation and orchestration services.

-
IT Power Solutions
IT Power Solutions
NO MORE DOWNTIME
Enjoy continuous and stable supply of electricity to critical IT infrastructure. Using a wide range of technologies and systems from Uninterruptible Power Supplies (UPS) that protect against power interruptions to energy-efficient inverters that optimize power conversion, keep your digital world running smoothly

-
Fire Detection and Suppression
Fire Detection and Suppression
SECURE YOUR DATA
The combination of fire detection and suppression delivers the best result to save your data center infrastructure in the event of fire. It is specifically designed to sense heat and automatically start the process of suppression.
-
Inventory and Asset Management
-
Telecom
- Partner with us

-
OEM / Vendor
OEM / Vendor
TOGETHER WE CAN DO MORE
Our aim is to change the technology landscape in Africa. To achieve that we believe in collaboration. Join the 247 Tech ecosystem and let us digitally transform the continent.

-
Request for evaluation
Request for evaluation
GET A FREE EVALUATION TODAY
We offer free evaluation and advisory services to help you choose the right solutions for your company.

-
Request for evaluation
-
Reseller
Reseller
A PARTNERSHIP THAT EXPAND YOUR POSSIBILITIES
At 247 we offer our resellers great products, technical and financial support and the training you need to serve your clients.
-
Request for evaluation
Request for evaluation
GET A FREE EVALUATION TODAY
We offer free evaluation and advisory services to help you choose the right solutions for your company.

-
Request for evaluation
-
Regional Representative
Regional Representative
REGIONAL REPRESENTATIVE LOCATOR
Find an authorized 247 regional representatives near you
-
Request for evaluation
Request for evaluation
GET A FREE EVALUATION TODAY
We offer free evaluation and advisory services to help you choose the right solutions for your company.

-
Request for evaluation
-
Alliances
Alliances
COLLABORATIONS THAT CREATE OPPORTUNITIES
The world today does not want multiple solutions from multiple vendors. They want one! That is why we create alliances with reputable organizations to offer bundled solutions that meet the needs of the modern business.
-
Request for evaluation
Request for evaluation
GET A FREE EVALUATION TODAY
We offer free evaluation and advisory services to help you choose the right solutions for your company.

-
Request for evaluation
-
Partner application
Partner application
BUILD YOUR SUCCESS WITH 247 TECH
Join our strong partner program and receive all the resources and support you require to deliver value to your clients and increase your revenue stream.

-
Partner application
BUILD YOUR SUCCESS WITH 247 TECH
Join our strong partner program and receive all the resources and support you require to deliver value to your clients and increase your revenue stream.

-
-
Find a Partner
Find a Partner
247 TECH PARTNER LOCATOR
Find an authorized and qualified 247 Tech partner near you
-
Find a Partner
247 TECH PARTNER LOCATOR
Find an authorized and qualified 247 Tech partner near you

-
-
Login to Partner Portal
-
OEM / Vendor
- Resources & Support

-
Technical Resources
Technical Resources
Get our latest publications and develop your technical expertise
Get up to date white papers and research documents

-
Technical Resources
Get our latest publications and develop your technical expertise
Get up to date white papers and research documents

-
-
Connect for Support
-
Downloads
Downloads
Download our latest product documents and resources
Explore our product and service brochures and documents

-
Downloads
Download our latest product documents and resources
Explore our product and service brochures and documents

-
-
Training
Training
Access our latest trainings and certifications
Get comprehensive business and technical training for you and your team

-
Training
Access our latest trainings and certifications
Get comprehensive business and technical training for you and your team

-
-
Technical Resources
- Why 247

-
Our Support
Our Support
OUR CUSTOMERS COME FIRST
Enjoy speed in response, and efficient technical support or guidance

-
Our Support
OUR CUSTOMERS COME FIRST
Enjoy speed in response, and efficient technical support or guidance

-
-
Our Team
Our Team
A TEAM COMMITTED TO BUILDING YOUR VISION
We boast a large team that has diverse subject matter experts who offer the right technical advice, understand project management and implementation while upskilling your technical knowledge.

-
Our Team
A TEAM COMMITTED TO BUILDING YOUR VISION
We boast a large team that has diverse subject matter experts who offer the right technical advice, understand project management and implementation while upskilling your technical knowledge.

-
-
Our Approach
Our Approach
SETTING THE BENCHMARK IN THE INDUSTRY
We take the time to understand the crux of the problem when working with a client, to ensure we offer products and services that are guaranteed to meet the customers’ needs

-
Our Approach
SETTING THE BENCHMARK IN THE INDUSTRY
We take the time to understand the crux of the problem when working with a client, to ensure we offer products and services that are guaranteed to meet the customers’ needs

-
-
Our Reach
Our Reach
SERVICE ACROSS BORDERS
247 Tech is present across Africa. Having experience executing projects across borders from logistics, implementation to post-sales support, we understand how to serve companies present in multiple geographies
-
Our Reach
SERVICE ACROSS BORDERS
247 Tech is present across Africa. Having experience executing projects across borders from logistics, implementation to post-sales support, we understand how to serve companies present in multiple geographies

-
-
Our Support
- Company

-
Who We are
Who We are
REVOLUTIONIZING THE WAY TECHNOLOGY IS DELIVERED
We are 360 technology solution provider with one goal; to change the way technology is delivered to businesses across the globe.
-
Who We are
REVOLUTIONIZING THE WAY TECHNOLOGY IS DELIVERED
We are 360 technology solution provider with one goal; to change the way technology is delivered to businesses across the globe.

-
-
Leadership
Leadership
THE BRAINS BEHIND 247 TECH
Our leadership team has years of experience in technology. They are industry experts committed to building a global technology company with an enthusiastic culture that offers value to all its stakeholder

-
Leadership
THE BRAINS BEHIND 247 TECH
Our leadership team has years of experience in technology. They are industry experts committed to building a global technology company with an enthusiastic culture that offers value to all its stakeholder

-
-
Coverage
Coverage
SERVING CLIENTS ACROSS AFRICA
We are a fast growing company, with branches in four African countries; Kenya, Tanzania, Egypt and Nigeria as well as offices in the UAE.
-
Coverage
SERVING CLIENTS ACROSS AFRICA
We are a fast growing company, with branches in four African countries; Kenya, Tanzania, Egypt and Nigeria as well as offices in the UAE.

-
-
CSR
CSR
Empowering Communities, Inspiring Change
We believe in making a difference beyond business. Through our Corporate Social Responsibility (CSR) initiatives, we are committed to empowering communities, fostering sustainability, and driving positive change.
-
CSR
Empowering Communities, Inspiring Change
We believe in making a difference beyond business. Through our Corporate Social Responsibility (CSR) initiatives, we are committed to empowering communities, fostering sustainability, and driving positive change.
-
-
Careers
Careers
JOIN FOR THE OPPORTUNITY STAY FOR THE CULTURE
Become part a thriving company with an enthusiastic culture. We are passionate about developing the expertise of our people and creating an inclusive work space.

-
Careers
JOIN FOR THE OPPORTUNITY STAY FOR THE CULTURE
Become part a thriving company with an enthusiastic culture. We are passionate about developing the expertise of our people and creating an inclusive work space.

-
-
Investors
Investors
A COMPANY DRIVEN BY PURPOSE
247 TECH is changing the African landscape with technology solutions that deliver excellent experiences and unlocks productivity for enterprises in the continent.
-
Investors
A COMPANY DRIVEN BY PURPOSE
247 TECH is changing the African landscape with technology solutions that deliver excellent experiences and unlocks productivity for enterprises in the continent.

-
-
Who We are
- Insights

-
Join hands for the future
Join hands for the future
INNOVATIONS THAT ARE MAPPING THE FUTURE
We leverage the power of technology help you build the business of the future today!

-
Digital Transformation
Digital Transformation
ENHANCE YOUR AGILITY
Build a company that sets the standard and moves fast and efficiently through technology.

-
Artificial Intelligence
Artificial Intelligence
DISCOVER THE POWER OF AI
This is the future of technology. Discover how to take advantage of business opportunities using artificial intelligence.
-
Software Defined Networking
Software Defined Networking
INTENT-BASED NETWORKING
Automate your complete network lifecycle for simpler operations, faster troubleshooting and improved security

-
Cloud Migration
Cloud Migration
ENJOY MORE CAPACITY FOR YOUR BUSINESS
Leverage efficient scalability, easy management and undeniable power for your business by moving to the cloud.

-
Internet of Things
Internet of Things
AN ECOSYSTEM OF INFORMATION
IOT is transforming everyday objects into sources of information. Learn how to leverage it for your business.
-
Robotics
Robotics
THE FUTURE IS NOW
Be ahead of the curve and discover robotics is transforming your industry.

-
Blockchain
Blockchain
REAL-TIME AND TAMPER PROOF
Enjoy data integrity with a single source of information, zero duplication and increased data security.
-
Digital Transformation
-
Newsroom
-
Blogs
Blogs
BE IN THE KNOW
Explore the latest ideas and insights on technology as well as out thought leadership articles.

-
Blogs
BE IN THE KNOW
Explore the latest ideas and insights on technology as well as out thought leadership articles.

-
-
Events
Events
DISCOVER OUR LATEST EVENTS
Join us for our innovative and interactive social gatherings, exhibitions, webinars and workshops.

-
Events
DISCOVER OUR LATEST EVENTS
Join us for our innovative and interactive social gatherings, exhibitions, webinars and workshops.

-
-
Join hands for the future





